Integrated Application Security Checklist helps you deploy a secure application
Valid from Pega Version 7.3.1
Pega® Platform now provides an Application Security Checklist that you can refer to when you prepare your application for deployment. By completing the recommended tasks in this checklist, you can track your progress, access instructional information for tasks, and verify that your configurations are secure.
For more information, see Preparing your application for secure deployment, Compliance Score tab, Designer Studio — Home page.
Certain flow actions deprecated and replaced
Valid from Pega Version 7.1.7
To ensure compatibility with supported browsers and mobile devices and to enhance ease of design, the following flow actions are deprecated and replaced. As a best practice, use the replacement actions for new development. The deprecated rules are still supported and do not have to be updated.
| Deprecated | Replacement |
|---|---|
| Transfer | Transfer Assignment |
| TransferAdvanced | " |
| TransferToManager | " |
| TransferToWorkbasket | " |
| Approve | Approval |
| Reject | " |
| AttachAFile | Attach Content |
| pyAdjustSLA | Adjust Assignment SLA |
| pyAdjustSLATimes | " |
| pyChangeAssignmentSLA | " |
| pyUpdate | Update Case |
For example, the new Transfer Assignment action supports the most common routing options such as operator, workbasket, and reporting manager. Advanced options allow users to escalate, set due dates, update status, and provide instructions.
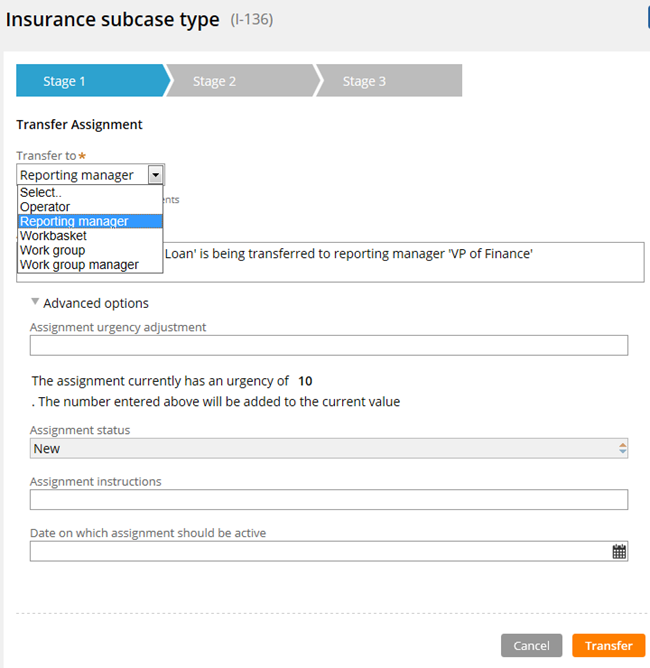
Transform Assignment form
See Atlas - Standard Flow Actions (Local).
Use of the @java function in expressions is deprecated
Valid from Pega Version 7.3.1
Use of the @java function in expressions is deprecated. Use a utility function or other product feature instead.
For more information about expressions, see Building expressions with the Expression Builder.
Pega API available in Pega Express
Valid from Pega Version 7.4
The Pega® API is now included on the Channels and Interfaces dashboard in Pega Express. You can configure Pega APIs to access Pega application functionality directly from Pega Express without switching to Designer Studio.
For more information about channel interfaces, see Channels and interfaces. For more information about the Pega API.
Deprecated metadata types in the Connector and Metadata wizard
Valid from Pega Version 8.2
The WSDL, SAP WSDL, and DTD metadata types have been deprecated in the Connector and Metadata wizard. For WSDL, use SOAP integration, and for DTD, use XSD.
For more information about SOAP connectors, see About Connect SOAP rules. For more information about XSD, see About the Connector and Metadata wizard.
DCO Compatibility tool is deprecated
Valid from Pega Version 8.1
The DCO Compatibility tool has been deprecated. Use the Application Guardrails landing page to see the compliance score and any warnings for your application.
For more information, see Application Guardrails landing page.
Pega Client for Windows
Valid from Pega Version 7.2.2
Pega Client for Windows is a stand-alone application that serves as a container for Pega 7 Platform applications. The target for this product is Windows 10 laptops and tablet devices. It communicates directly with the Pega 7 Platform server to support online and offline-enabled applications. Pega Client for Windows works on 32-bit (x86) and 64-bit (x64) Windows devices.
For more information, see Features and functions of the Pega Client for Windows.
Deprecation of override rulesets in run-time ruleset lists
Valid from Pega Version 7.2.1
Pega 7.2.1 is the last release where override rulesets can be incorporated in the run-time ruleset list. The ability to create override rulesets was originally deprecated in Pega 7.1. However, any override rulesets that were created in releases prior to Pega 7.1 in the application ruleset lists were still incorporated into the run-time ruleset lists at the appropriate location. In releases after Pega 7.2.1, override rulesets will be ignored and will not be incorporated in the run-time ruleset list. Therefore, it is recommended that you use production rulesets in access groups instead of override rulesets.
CyberArk password vault support added for Pega database
Valid from Pega Version 8.3
With the CyberArk password vault, you can store your systems' passwords in a secure, central location and retrieve them from that location instead of directly entering credentials into the systems. This support is available only for IBM WebSphere environments.
For more information, see Pega Platform deployment guides.
For Microsoft SQL Server deployments, change settings to create data types in Integration Designer
Valid from Pega Version 8.1
For on-premises deployments that use Microsoft SQL Server, set the Pega-Reporting/reporting/useMergeHintForRRquery dynamic system setting to true. If you do not configure this setting, you might not be able to create a new data type in Integration Designer that uses Pega as the system of record. Configure the setting as follows:
- Owning ruleset: Pega-Reporting
- Setting purpose: reporting/useMergeHintForRRquery
- Value: true
For more information about configuring dynamic system settings, see Creating a dynamic system setting.

