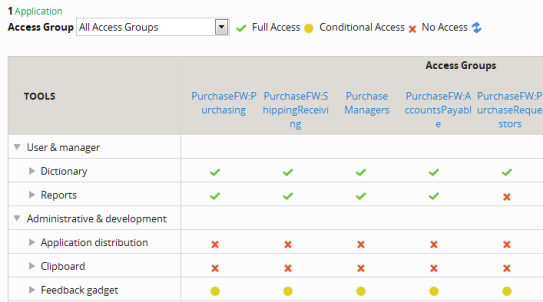
When a tool category is expanded, icons indicate full access, no access, or conditional access granted to members of the access group.
Summarized views can alert you to areas in your business processes that need tighter restrictions. You can easily expand the view to edit the authorizations of a role.
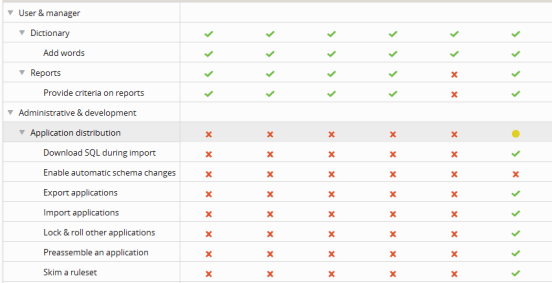
For example, if the tool is Add Words, a next to it indicates all users in the selected access group can add words to the spell check dictionary.
This table describes the location in the system of each tool. You can place your pointer over a tool name to display a descriptive tool tip.
Your access group should provide Full or Conditional Access to the “AccessManager: change authorizations” tool in order to edit authorization settings in Access Manager. You cannot edit standard Pega 7 Platform roles.
Tool Category
|
Tool Name
|
Description/Result
|
| User & manager |
|
Tools intended for end users. These tools do not affect rule definitions. |
| Dictionary |
Add words |
Add words to the spell check dictionary.
When authorized, an operator can right-click on a word flagged by the spell checker and add it to the dictionary.
|
| Reports |
Provide criteria on reports |
Provide selection criteria on reports.
When authorized, an operator can view the Available Values tab on the Pick Values pop-up when customizing criteria for a report.
|
| Administrative & development |
|
Tools intended for system architects and developers. They can impact run time system display and behavior for end users.
|
| Application distribution |
Download SQL during import |
View and download SQL during application import for database administration.
When authorized, an operator can access Designer Studio > Application > Distribution > Import.
|
| |
Enable automatic schema changes
|
Enable automatic schema changes during application import.
When authorized, an operator can access Designer Studio> Application > Distribution > Import.
|
| |
Export applications |
Export applications.
When authorized, an operator can access Designer Studio > Application > Distribution > Export. When set to No Access, the system displays an error message when the operator attempts to export.
|
| |
Lock & roll other applications |
Lock & roll other applications.
When authorized, an operator can access Designer Studioshor > Application > Structure > Other Applications. The Other Applications tab lists applications and Lock & Roll buttons.
|
| |
Preassemble an application
|
Run the static assembler on demand to preassemble an application.
When authorized, an operator can access Designer Studio > System > Assembly> Static Assembler.
|
| |
Skim a ruleset |
Skim a RuleSet.
When authorized, an operator can access Designer Studio > System >Refactor> RuleSets > Skim a RuleSet.
|
| Clipboard |
Execute activity on page
|
Execute an activity on a page in clipboard.
When authorized, an operator can view the clipboard, click a page and click Execute Activity on the Actions menu (the Execute Activity window pops up). When set to No Access, the Execute Activity item is displayed inactive on the Actions menu.
|
| Feedback Gadget |
Use the feedback gadget |
Use the feedback gadget.
When authorized, an operator can see the gadget and send message normally.
|
| Message queue management |
Modify JMS queue
|
View, add and remove messages on a JMS queue |
| |
View JMS queue |
View JMS message queue |
| |
Modify MQ queue |
View, add and remove messages on a MQ queue.
When authorized, an operator can access Designer Studio > Integration > Resources > Servers > MQ Servers. Operator can select a server and modify MQ messages.
|
| |
View MQ queue |
View MQ message queue.
When authorized, an operator can access Designer Studio > Integration > Resources > Servers > MQ Servers. Operator can select a server and view the MQ messages queue.
|
| Reports |
Optimize property
|
Use the one-click property optimization wizard.
When authorized, an operator can access Designer Studio > System > Database > Column Population Jobs.
|
| |
Optimize schema |
Use the schema optimization wizard.
When authorized, an operator can access Designer Studio > System > Database > Modify Schema.
|
| Rules & rulesets |
Private check-out |
Perform private check-out / check-in of rules
When authorized, an operator can perform private edits on locked rulesets. The system displays the Private Edit button.
|
| Security |
AccessManager: change authorizations
|
Change role based access using Access Manager
When authorized, an operator can access Designer Studio > Org & Security > Access Manager > Work & Process / Tools. Operator can modify authorizations in grids.
|
| |
AccessManager: view authorizations |
View role based access using Access Manager.
When authorized, an operator can access Designer Studio > Org & Security > Access Manager > Work & Process / Tools. Operator can view but not edit authorizations in grids.
|
| |
Configure system security policy settings |
Adjust the security policy rules for operator IDs and passwords, brute-force attack mitigation with CAPTCHAs and audit levels.
When authorized, an operator can access Designer Studio > System > Settings > Security Policies.
|
| |
Rule security analyzer |
Use the rule security analyzer.
When authorized, an operator can access Designer Studio > Org & Security > Tools > Security > Rule Security Analyzer.
|
| Tracer |
Advanced tracer options
|
Use tracer breakpoints and watch variables.
When authorized, an operator can access the Tracer button on the Designer Studio toolbar and the Tracer tool displays the Breakpoints and Watch buttons on its toolbar.
|
| |
Basic tracer options |
Use settings, configure tracer output, use play and pause, and view details for any row.
When authorized, an operator can access the Tracer button on the Designer Studio toolbar and the Tracer tool displays the Settings button on its toolbar. The system displays details on tracer events when a row is clicked.
|
| |
Use remote tracer |
Use remote tracer to connect to another requestor session.
When authorized, an operator can access the Tracer button on the Designer Studio toolbar and the Tracer tool displays the Remote Tracer button on its toolbar.
|
| User interface |
Toolbar: New button
|
When authorized, an operator can use the New button in Designer Studio.
|
| |
Toolbar: Preview button |
When authorized, an operator can use the Preview button in Designer Studio.
|
| |
Toolbar: Run button |
When authorized, an operator can use the Run button in Designer Studio.
|
| |
Toolbar: Save As button |
When authorized, an operator can use the Save As button in Designer Studio.
|
| |
Live UI tool |
When authorized, an operator can use the Live UI tool.
|
The list of standard tools available to secure in Access Manager cannot be changed. The Tools tab is populated by the data transform rule pxPopulateTools. However, this rule can apply another data transform rule, pyPopulateTools, to append other tools you define in pyPopulateTools to the bottom of the Tools tab. For more information, see PDN article Adding custom tools to Access Manager.
You cannot modify authorizations when viewing all access groups. The display is intended to show you only whether all operators in each access group are fully authorized to access every tool in a tool category ( ), or all are denied authorization for every user action (
), or all are denied authorization for every user action ( ) -- or whether there is some mix of authorizations among the user actions (
) -- or whether there is some mix of authorizations among the user actions ( ). Refer to the example below. A tool category might be Application distribution; tools in it include Import applications or Skim a RuleSet.
). Refer to the example below. A tool category might be Application distribution; tools in it include Import applications or Skim a RuleSet.
 ), or all are denied authorization for every user action (
), or all are denied authorization for every user action ( ) -- or whether there is some mix of authorizations among the user actions (
) -- or whether there is some mix of authorizations among the user actions ( ). Refer to the example below. A tool category might be Application distribution; tools in it include Import applications or Skim a RuleSet.
). Refer to the example below. A tool category might be Application distribution; tools in it include Import applications or Skim a RuleSet.