Guardrails compliance score
Valid from Pega Version 7.1.5
The Application Guardrails landing page has been enhanced to help you build more guardrail-compliant applications. Increase transparency and accountability on your projects by responding to the following compliance score metrics:
- A weighted compliance score (0-100) based on warnings, severity, and justification
- A percentage of compliant rules in your application
- Total number of rules in your application
- Total number of rules in your application with warnings (justified and unjustified)
Additional metrics include alert and interaction count trends over the last four weeks.
For more information, see Guardrails compliance score.
Access Manager portal
Valid from Pega Version 7.1.5
Changes to the Access Manager simplify the process of modifying the access rights of features for an application. The changes, including creation of an Access Manager portal, make it easier for non-technical users, such as business architects, to set access rights even if they may not have a deep understanding of Pega 7's security model and class inheritance structure.
Directed inheritance view in Application Explorer
Valid from Pega Version 7.1.5
You can now specify which inheritance model is used to populate classes in the Application Explorer. From the top level menu, use the “Explorer Inheritance” option to choose between:
- Pattern: only display class names whose prefix matches the root node class name.
- Directed: first display classes that explicitly name the root node as the parent class; then display classes with pattern inheritance.
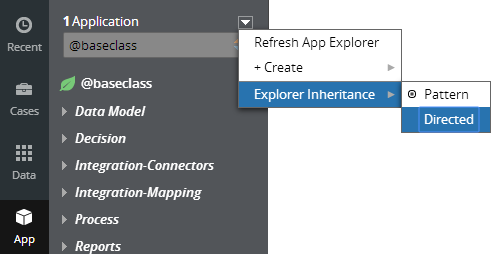
By default, the Application Explorer loads using Pattern inheritance.
Save Application Explorer filter selections
Valid from Pega Version 7.1.5
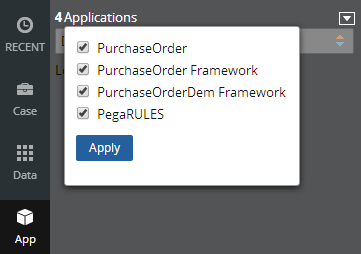
Application scoping control selections made in the Application Explorer are now persisted between sessions. These preferences are stored in an operator record on an access group level. If you delete (and later re-add) an access group on your operator form, the application scoping control defaults to all layers selected:
External access control DASS
Valid from Pega Version 7.1.5
A new Dynamic Admin System Setting (DASS) controls the Designer Studio's access to external systems, specifically the PDN RSS feed found on the home page.
By default, Pega-Desktop.AllowAccessToExternalSystem is set to TRUE. Update this setting to FALSE to hide the PDN RSS feed and ensure that no RSS fetch is performed.
Add subspaces within spaces
Valid from Pega Version 8.2
You can now create subspaces within spaces. By adding a subspace, you can collaborate on a subtopic that is related to the topic of the parent space. For example, you can create an Annual Day subspace within the Events space.
For more information, see Creating a subspace.
All search data is encrypted
Valid from Pega Version 8.2
All search data in Pega Cloud deployments is now encrypted, both at rest and in transit. The encryption of search data makes search compliant with regulatory requirements.
For more information about search, see Full-text search.
Improve clipboard performance for Service REST
Valid from Pega Version 8.2
Improve clipboard performance in Service REST processing by using the new Lightweight clipboard mode option. This mode does not support all clipboard features.
For a list of supported and unsupported features, see Service REST form - Completing the Service tab.
Authentication service for basic credentials
Valid from Pega Version 8.2
A new type of authentication service is available for authenticating operators by using basic credentials (user ID and password). The default Pega Platform™ login is now an instance of this type of authentication service. All basic credentials authentication services include mobile authentication with the OAuth 2.0 protocol and Proof Key for Code Exchange (PKCE). You no longer have to create a custom authentication service to support mobile applications.
For more information, see Configuring a basic authentication service.
Unauthenticated sessions transition seamlessly to authenticated
Valid from Pega Version 8.2
A new authentication service type allows a guest user to use an application without logging in, and to be prompted to authenticate later in the session. This enhancement supports scenarios such as online shopping portals where a user can browse for items and load a shopping cart as a guest but be prompted for credentials at checkout.
For more information, see Configuring an anonymous authentication service.

