Attachment support for requirements
Valid from Pega Version 7.1.6
Requirements now support attachments. You can add attachments from the Designer Studio > Application > Profile > Requirements landing page, the Add/Edit Requirement modal, or the requirement rule form.
Enhanced document generation
Valid from Pega Version 7.1.6
The following usability improvements have been made to documents generated by the Application Document Wizard:
- Stages and Processes now appear for case types that use Case Lifecycle Management. This diagram includes hyperlinks to corresponding sections in the document and is scoped to top-level processes only.
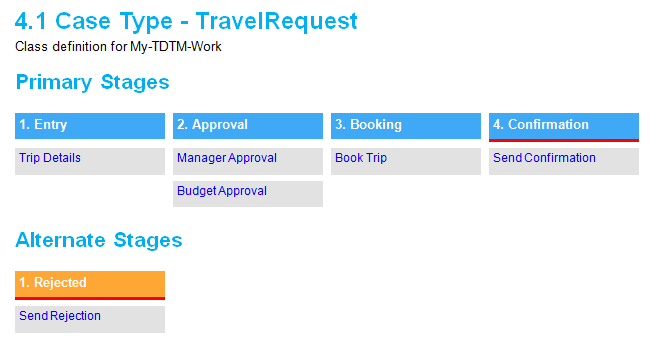
- All flows (excluding pyStartCase) referenced by a case type now appear in documents. This removes previous constraints on non-starting, draft, and checked out flows.
- Entity Relationship Diagrams (ERDs) are now embedded in documents as Visio objects.
- Sections without content are omitted from the generated document.
- Screenshots are labeled.
- Requirement text (Long Description) is included in the Requirements Matrix section.
- Linked requirements appear in context beneath their associated specification.
- Acceptance Criteria appears in context beneath the associated specification, report, or correspondence item.
Generate documents in the background
Valid from Pega Version 7.1.8
When you generate system documentation by using the Document Application wizard ( > > > ), the process now runs on a server and not on your local client system. This change not only generates your document more quickly, but also allows you to multi-task within Pega 7 while your document is generating in the background. When the generation is completed, download the document to your computer.
For more information, see:
Updating customized Application Document templates with server-side document generation
Screenshot generation still runs on local client
Warning message when opening server-generated documents
Screenshot generation runs on local client
Valid from Pega Version 7.1.8
If you generate screenshots to include in your application document, this process still runs on your local client. Additionally, you are still required to use Internet Explorer to use this feature.
Warning message when opening server-generated documents
Valid from Pega Version 7.1.8
Depending on your system configuration, the following warning message might be displayed when you open a document that was generated on the server.
If you click , certain content (for example, Table of Contents) is not populated in the document. Instead, click and save the document.
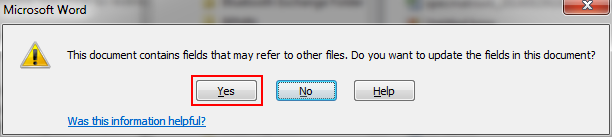
The warning message that displays
Link URLs to applications, requirements, and specifications
Valid from Pega Version 7.1.8
In addition to files, you can now attach URLs to applications, requirements, and specifications by using the Add/Edit Attachment modal dialog box in Pega 7. This change allows you to link directly to dynamic content in other URL-based systems rather than link to a static file of that content.
New JWT access token format: Authorized Access Token
Valid from Pega Version 8.5
Pega Platform™ is changing from using opaque tokens to using JSON Web (JWT) tokens and the JWT access token format: Authorized Access Token (AAT). An AAT enables a client application to validate the server for user permissions and authorizes a specific application to access specific parts of a user’s data.
The major benefits to using the JWT format are:
- The JWT is a self-contained token that has authentication information, expire time information, and other user-defined claims digitally signed.
- A single token can be used with multiple applications.
- The tokens are short-lived and can minimize damage if transport security is compromised, as the token signature is verified.
- As the token is verified with the signature, there is no need to verify against a database, thus reducing latency (usually important for Web APIs).
For more information, see Understanding authorized access tokens.
Improvements to OAuth 2.0 Services with Token Introspection Service and Token Denylist Service
Valid from Pega Version 8.5
Increase the security of user sessions by using the newly supported Token Introspection and Denylist services for OAuth 2.0.
Token Introspection service
Use the Token Introspection service to validate JSON Web Tokens (JWT). The Token Introspection service requires authentication.
Pega now uses OAuth 2.0 access tokens called Authorized Access Tokens (AAT).
Token Introspection service endpoint
The Token Introspection service endpoint provides the information about the status of access token and refresh token. Token introspection can be used to validate if a given token is still active or inactive. The token introspection endpoint determines whether the token is valid. The status indicates whether an access token or refresh token is valid or invalid:
- Valid tokens have the
“active”:truestatus - Invalid tokens have the
“active” :falsestatus.
The inactive status can also be due to revocation.
Token Denylist service
You can add tokens to the deny list in cases where suspicious activity might have occurred. The Token Denylist service provides a method for denying user access to the application by revoking the user's access token. This service can prevent a token from being used more than the specified number of times, which can be helpful in preventing replay attacks. Stolen tokens should be revoked using this service. A GET API is also available to get the list of denied tokens.
Keys endpoint
Pega Platform™ is changing from using opaque tokens to JSON Web (JWT) tokens. If this JWT is used by any other system, the public key is needed for signature verification. A new endpoint is exposed to provide these public keys in JWK format: https://host:port/prweb/api/oauth2/v1/token/keys.
For more information, see OAuth 2.0 Management Services.
Enhanced refresh token strategy
Valid from Pega Version 8.5
You now have more precise control over your refresh token expiration strategy. When a refresh token is enabled, you can choose to set its initial expiration based on the value provided by the IDP. The refresh token expiry can be derived from IDP’s session timeout when SSO is used with external IDP for user authentication in the authorization code grant flow. You can also specify a separate refresh token expiration strategy based on your use-case.
These can be configured in the OAuth2 Client registration rule form.
For more information, see Enhanced refresh token strategy.
Enhancements to token lifetime limits
Valid from Pega Version 8.5
Pega Platform™ uses OAuth 2.0 authorization codes, access tokens, and refresh tokens to provide flexible token-based security for applications. Expiration settings for these codes and tokens now adhere to certain strict value range based on industry leading practices. For example, the lifetime specified for the authorization code must be in the range 1-600 seconds.
These can be configured in the OAuth2 Client registration rule form.
For more information, see OAuth 2.0 Management Services.

