Application Express and the Content Security Policy
Valid from Pega Version 7.1.7
Application Express copies (if defined) the Content Security Policy (CSP) name (pyContentSecurityPolicyName) from the built-on application in a new application. It also sets the CSP mode (pyContentSecurityPolicyMode) to report. The values appear in the Content Security area on the application rule's Integration & Security tab.
When checking an application in the DCO Compatibility tool, a warning appears if the CSP name is missing.
Tracked changes persist between client sessions
Valid from Pega Version 7.1.7
The Microsoft Word native change tracking feature persists between client sessions for specifications. Enable this feature to facilitate collaborative reviews of your specifications with project stakeholders.
Inserting your specification updates as tracked changes allows you to:
- Provide visible markup to the next reviewer.
- Correlate edits to a specific user and time.
- Generate documents that include markup and comments.
Local settings, such as the colors you specify for markup, do not persist between clients.
For instructions on how to prevent markup and comments from appearing in generated documents, see Advanced options for editing specifications.
Add multiple attachments at once
Valid from Pega Version 7.1.7
You can now add more than one attachment to a requirement or specification at a time, without closing the Add/Edit Attachment modal dialog box. Use the traditional browse method to upload an attachment or drag and drop a local file, based on your needs. View and access your attachments from the Application Profile landing page, Requirement form, or Specification form.
Plan projects using release data
Valid from Pega Version 7.1.7
Requirements and specifications can now be mapped to a target release and iteration within a specific release. Populating these fields allows you to set and publish a release schedule through worksheets generated by the Sizing wizard. Access these fields from the Application Profile landing page or by opening any requirement or specification.
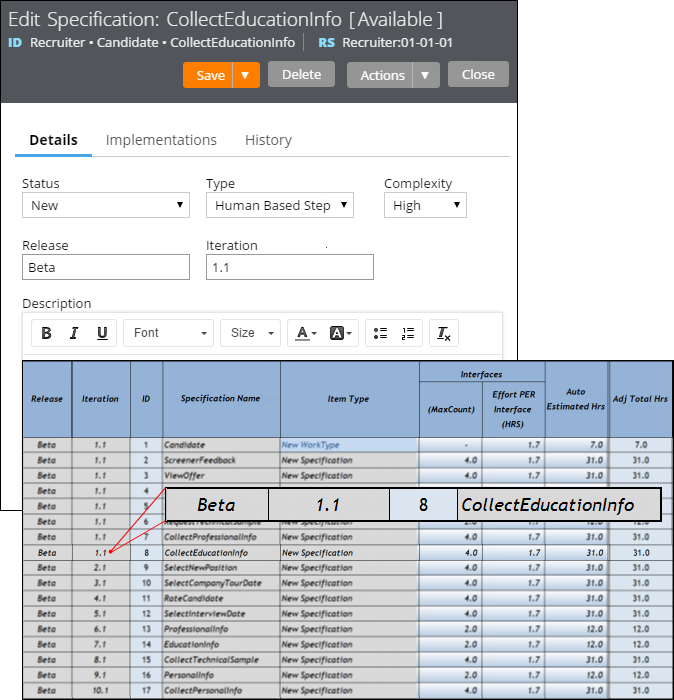
The Release and Iteration fields as they appear in a specification and a corresponding worksheet
The Sizing wizard incorporates values from the Release and Iteration fields for specifications only.
Specification type extended for decisioning users
Valid from Pega Version 7.1.7
Specifications now support a Decision Strategy Manager (DSM) type. This allows you to map your specifications to a decisioning component, such as a strategy or model. After you select an appropriate subtype and provide relevant metadata, you can run the Sizing wizard to incorporate these details into project sizing worksheets.

DSM specification details as they appear in the Specification form and Sizing wizard output
You must have access to Decision Management rulesets to create DSM specifications. For more information on specification types, refer to the Details tab of the Specification form. To view all specifications in your application, filtered by type, refer to the Application Profile landing page.
Add collections as linked implementations
Valid from Pega Version 7.1.7
You can now identify a collection or individual steps within a collection as an implementation of a specification. Linking specifications to rules allows you to more accurately convey your application design to project stakeholders. Use the Specifications tab on the Collection form to create these links.
To see all implementations for a given specification, refer to the Application Profile landing page or the Implementations tab of the Specification form.
Add project branding to generated documents
Valid from Pega Version 7.1.7
The standard Word Template for specification descriptions is now extensible. Using a customized template allows you to brand your generated documents with project-specific elements.
Specialize the Rule-Application-UseCase.pySpecificationDescription rule to:
- Include relevant images such as company logos.
- Define static text.
- Insert dynamic elements by merging clipboard values into field codes.
Generated document with custom company logo
Refer to Advanced options for editing specifications for instructions on how to override this template.
Password hashing using SHA-256/SHA-512
Valid from Pega Version 7.1.7
Password hashing using the SHA-256 and SHA-512 hash functions is available for use during the the Pega 7 authentication process with operator, ruleset, and update lock passwords. The SHA-256/SHA-512 hash functions join the previously available MD5 and SHA-1 hash functions.
Using SHA-256/SHA-512 hashing when creating or upgrading a password hash results in increased complexity of the hash, making it extremely difficult and time-consuming to determine hashed password values stored in a database.
Note that once you have updated your system to Pega 7.1.7 and have applied password hashing using the SHA-256/SHA-512 hash functions, reverting back to a previous version of Pega 7 is not advised as this causes hashed passwords using SHA-256/SHA-512 to fail.
See About password hashing for more information.
Support for the JSON Web Token Bearer grant type for accessing external APIs
Valid from Pega Version 8.4
You can now access external APIs by using the new OAuth 2.0 JSON Web Token (JWT) Bearer grant type, in an OAuth 2.0 authentication profile. To use the JWT Bearer grant type as a client assertion, source the JWT from an active SSO session, a token profile, or a property reference. You can use JWTs that you obtain during an OpenID Connect SSO in connectors, to achieve user impersonation flows, such as the On-Behalf-Of (OBO) flow. The OAuth 2.0 type authentication profile now also supports authentication of client applications by using Private Key JWTs.
Instances of the OAuth 2.0 provider are now deprecated. As a best practice, use the new, unified authentication profile configuration instead.
For more information, see Configuring an OAuth 2.0 authentication profile.
Upgrade impact
After an upgrade to Pega Platform 8.4 and later, Authentication Profiles can take advantage of the new JWT based OAuth 2.0 grant type and client authentication features. To take advantage of this and other new security features, you must update any existing Authentication Profiles formats must to use those in Pega Platform 8.4 and later.
What steps are required to update the application to be compatible with this change?
Since these features are available only for profiles created in Pega Platform 8.4 and later, clients must open and then save existing 'Authentication Profile' instances to ensure that the configuration is compatible with the latest authentication formats.
Sign and encrypt signatures and content with additional algorithms
Valid from Pega Version 8.4
You can now authenticate using JSON Web Token (JWT) token profiles to symmetrically and asymmetrically encrypt both signatures and content. All algorithms in the Nimbus JWT library are supported, including nested tokens. Custom key identifier headers (kid) are also supported. Use token profiles to securely propagate identities and transfer data between systems.
For more information, see Creating a processing JSON Web token profile.
For more information, see Creating a generation JSON Web token profile.

