Improved cross-browser support
Valid from Pega Version 7.1.7
All rule forms are now harness-based and open in the work area of Designer Studio. This means that you can develop in the browser of your choice, free from pop-up distractions and incompatibility messages. Many rule forms have been upgraded to use the latest layouts, styles, and design best practices, giving you a consistent development experience.

Viewing a Word Template in Pega 7.1.7 compared with Pega 7.1.6
Previous restrictions still apply to any deprecated or custom rule forms in your application that remain form-based. Refer to the Deprecated features list for guidance on how to upgrade these forms and recommended alternatives.
Quickly see what's new in Pega 7.1.7
Valid from Pega Version 7.1.7
A new home page panel gives you centralized access to Help and the PDN, eliminating the need to leave Designer Studio. Use the buttons in this panel to learn about new features quickly and stay connected to product announcements.

What’s new panel as it appears on the Designer Studio home page
After you are finished reviewing new features and enhancements, you can dismiss the What’s new panel. This hides the panel from your operator in future sessions without impacting the home page for other application users.
Clear and actionable guardrails help you mitigate risk sooner
Valid from Pega Version 7.1.7
The Application Guardrails landing page has been restructured to give you an executive-level view into your application health. Use the available metrics and tools on each tab to understand the scope of warnings in your application, the operators responsible for introducing this risk, and ways to improve your compliance score before your development goes into production.
Include this landing page in your governance process to:
- Understand your application compliance score and how it has changed over time:
A score of 90 or greater indicates your application is in good standing.
A score of 80-89 indicates your application needs review for improvement.
A score below 80 requires immediate action.
- Investigate the factors contributing to your score, such as warning age or severity, and the rules and operators associated with each warning.
- Review a comprehensive list of warnings and the recommended path to resolve them.
- Communicate all of these details to project stakeholders through email or exported documents.
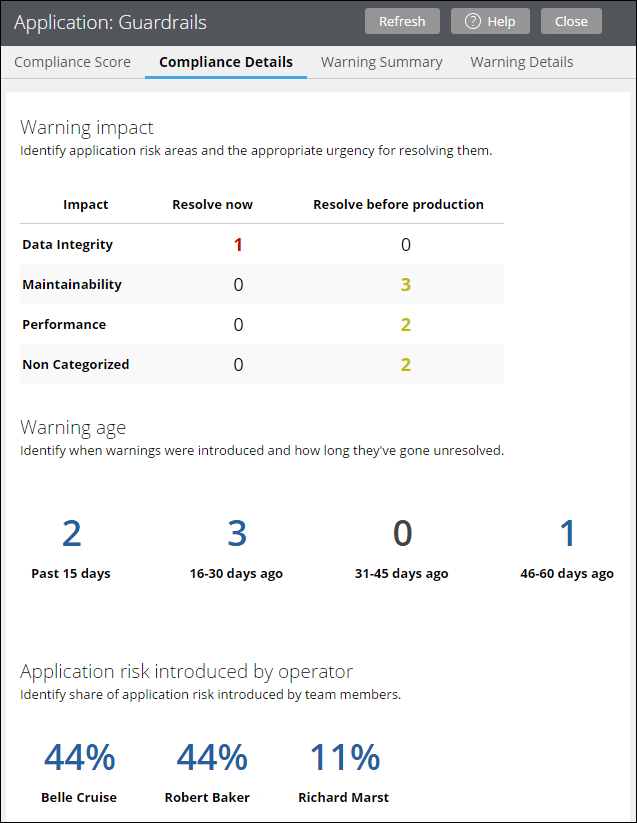
Available metrics on the Compliance Details tab of the Application Guardrails landing page
The Charts tab in this landing page has been superseded by the Compliance Details tab, which provides more options and an enhanced presentation.
For more information about the available features on all tabs in this landing page, see Application Guardrails landing page.
Password hashing using SHA-256/SHA-512
Valid from Pega Version 7.1.7
Password hashing using the SHA-256 and SHA-512 hash functions is available for use during the the Pega 7 authentication process with operator, ruleset, and update lock passwords. The SHA-256/SHA-512 hash functions join the previously available MD5 and SHA-1 hash functions.
Using SHA-256/SHA-512 hashing when creating or upgrading a password hash results in increased complexity of the hash, making it extremely difficult and time-consuming to determine hashed password values stored in a database.
Note that once you have updated your system to Pega 7.1.7 and have applied password hashing using the SHA-256/SHA-512 hash functions, reverting back to a previous version of Pega 7 is not advised as this causes hashed passwords using SHA-256/SHA-512 to fail.
See About password hashing for more information.
View status of custom search indexes
Valid from Pega Version 8.1
Custom search indexes are special purpose indexes that are created and managed outside of Pega Platform™. You can view the status of custom search indexes on the Search landing page to see whether they are complete. This information is useful for troubleshooting and can help you determine whether to rebuild the index.
For more information, see Checking search index status.
Job Scheduler and Queue Processor rules replace agents
Valid from Pega Version 8.1
The Job Scheduler rule and the Queue Processor rule replace agents and improve background processing. The Job Scheduler rule is used for recurring or scheduled tasks, such as sending summary emails on weekdays. This rule can be run on all nodes or on specific node types according to your customized pattern. The Queue Processor rule is used for tasks with no recurrence-based pattern. It provides scalability and capability for immediate or delayed message processing, such as submitting status changes to an external system. You can use a standard queue processor or a dedicated queue processor, depending on your processing needs.
Pega Platform™ provides a set of default queue processors and job schedulers. Corresponding agents are no longer available.
For more information about Job Scheduler and Queue Processor rules, see Job Scheduler, Replacing an agent with a Job Scheduler rule, Queue Processor, Replacing an agent with a Queue Processor rule.
Improve application test coverage by running multiple sessions
Valid from Pega Version 8.1
You can improve the test coverage of your application by using a new test coverage method - Application Coverage. Multiple users can perform coverage sessions which are aggregated into a single report. By using report metrics that show the number of rules that are covered and are not covered by tests, developers can identify which areas of the application need more test coverage.
For more information, see the Test Coverage landing page.
Support for OAuth 2.0 authorization code grant type
Valid from Pega Version 8.1
Pega Platform™ now supports the OAuth 2.0 authorization code grant type, which allows Pega Platform to act as an OAuth 2.0 access token provider for native applications on mobile and other devices. By using the authorization code grant type for mobile clients, you no longer need to implement a variety of standards for various authentication providers. The authorization code grant type also supports the Proof Key for Code Exchange standard (PKCE) for securing public clients.
For more information, see Creating and configuring an OAuth 2.0 client registration.
Use client-based access control to support EU GDPR requirements
Valid from Pega Version 8.1
You can use client-based access control (CBAC) to satisfy the data privacy requirements of the European Union General Data Protection Regulation (GDPR) and similar regulations. By using client-based access control, you can identify the personal data of clients and automatically process requests to view, update, or remove the data in a secure manner. You can also enforce restrictions on the use of this data in application functions.
For more information, see Client-based access control.
REST APIs added for management of agents and requestors
Valid from Pega Version 8.1
You can use new REST APIs to download a module version report or manage requestors and agents in Pega Platform™. For example, you can use a requestor REST API to end a requestor process, and you can use an agent REST API to start or stop an agent. These APIs allow external systems to report and manage Pega resources.
For more information, see Pega API for Pega Platform and Pega API.

