Tamper-proof Pega Web Mashup loading
Valid from Pega Version 8.5
To protect your application from hackers, Pega Web Mashup is now loaded in a more secure way. The system generates a channel ID in the mashup code for validation on the server, before passing the mashup request.
For more information, see Creating a mashup.
Upgrade impact
After an upgrade to Pega Platform 8.5, existing mashups, which do not have the channel ID parameter in their code, cannot load and users see the access control warning.
What steps are required to update the application to be compatible with this change?
If you need to maintain full availability of the mashup during the upgrade of the production environment, perform the steps in Migrating existing mashups.
Automatic separation of date input
Valid from Pega Version 8.5
Date fields in Date Time controls now automatically divide strings of input into days, months, and years. In single fields, the system adds slashes (/) as the user types the value. For example, an input string of 10102020 becomes 10/10/2020. In separate day/month/year fields, the system automatically switches from one field to the next as the user types the value. This enhancement improves the user experience by helping to users provide input in a more convenient and time-efficient manner.
For more information, see Configuring a Date Time control.
Improvements to OAuth 2.0 Services with Token Introspection Service and Token Denylist Service
Valid from Pega Version 8.5
Increase the security of user sessions by using the newly supported Token Introspection and Denylist services for OAuth 2.0.
Token Introspection service
Use the Token Introspection service to validate JSON Web Tokens (JWT). The Token Introspection service requires authentication.
Pega now uses OAuth 2.0 access tokens called Authorized Access Tokens (AAT).
Token Introspection service endpoint
The Token Introspection service endpoint provides the information about the status of access token and refresh token. Token introspection can be used to validate if a given token is still active or inactive. The token introspection endpoint determines whether the token is valid. The status indicates whether an access token or refresh token is valid or invalid:
- Valid tokens have the
“active”:truestatus - Invalid tokens have the
“active” :falsestatus.
The inactive status can also be due to revocation.
Token Denylist service
You can add tokens to the deny list in cases where suspicious activity might have occurred. The Token Denylist service provides a method for denying user access to the application by revoking the user's access token. This service can prevent a token from being used more than the specified number of times, which can be helpful in preventing replay attacks. Stolen tokens should be revoked using this service. A GET API is also available to get the list of denied tokens.
Keys endpoint
Pega Platform™ is changing from using opaque tokens to JSON Web (JWT) tokens. If this JWT is used by any other system, the public key is needed for signature verification. A new endpoint is exposed to provide these public keys in JWK format: https://host:port/prweb/api/oauth2/v1/token/keys.
For more information, see OAuth 2.0 Management Services.
Search and Reporting does not index large items
Valid from Pega Version 8.5
When using the Search and Reporting (SRS) microservice in Pega Platform™ 8.5, you might encounter problems with indexing large out-of-the-box rules. The issue is not visible in Queue Processors, but you can access logs to verify which items the system does not index.
Improved identification and handling of code assembly errors
Valid from Pega Version 8.5
Code assembly error logs are now more meaningful and help you identify root causes with better accuracy. Pega Platform™ now also invalidates erroneous assembly to facilitate successful reassembly when the code is accessed again. For example, if a section is not correctly assembled when a user first signs in to the system, the application attempts to reassemble that section the next time a user signs in. In this way, you can avoid lingering issues and improve stability.
Enhanced tables in Cosmos React UI
Valid from Pega Version 8.5
The Pega Platform™ Cosmos React UI environment now includes improved tables. The updated tables use a revamped graphic design and support a number of new run-time behaviors, including column freezing and advanced filtering. The added features improve the user experience by giving case workers more control over data in tables, while the revised architecture enhances efficiency and reliability.
Response timeout configuration for predictions
Valid from Pega Version 8.5
You can now set a response timeout for your predictions in Prediction Studio. By setting a response timeout, you control how Prediction Studio registers customer responses that later serve as feedback data for your predictions.
For more information, see Customizing predictions.
Service levels for case stages
Valid from Pega Version 7.1.5
Service levels are available for stages in stage-based case management applications.
The service level starts when a case enters a stage and stops when it exits. The service level is defined in the Service level for stage field on the "Stage Configuration" dialog, which is accessed on the Case Designer Stages and Processes tab.
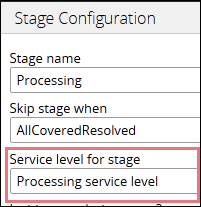
Alternatively, you can add a stage service level on the case type record's Stages tab.
Data APIs support data exploration in React UI tables
Valid from Pega Version 8.5
Data APIs have been enhanced to support filtering, sorting, paging, and aggregation in React UI tables. You can use that functionality to access your data quickly and intuitively. For example, by using paging, you can query a data page to retrieve the second page of an employee contact list and specify the number of results that are displayed on the page.
For more information, see Data API performance and limitations.
Enhancements to token lifetime limits
Valid from Pega Version 8.5
Pega Platform™ uses OAuth 2.0 authorization codes, access tokens, and refresh tokens to provide flexible token-based security for applications. Expiration settings for these codes and tokens now adhere to certain strict value range based on industry leading practices. For example, the lifetime specified for the authorization code must be in the range 1-600 seconds.
These can be configured in the OAuth2 Client registration rule form.
For more information, see OAuth 2.0 Management Services.

