Unit testing support for more rule types
Valid from Pega Version 8.3
You can now create unit tests for the following additional rule types. You can also create assertions to validate activity status. The expanded rule types for unit testing enable developers to more thoroughly perform regression testing of their application, thereby improving application quality.
- Collection
- Declare expression
- Map value
- Report definition
For more information about unit testing rules, see Pega unit test cases.
Upgrade impact
With the four new rule types, unit test execution and unit test compliance metrics will change. Reports on automated unit testing of the customer application decrease due to the increased pool of supported rules.
What steps are required to update the application to be compatible with this change?
After a successful upgrade, create Pega unit test cases for the newly supported rules to see updated and accurate unit test metrics.
Automatic retries for the SAVE operation on records
Valid from Pega Version 8.3
Batch and real-time data flow runs now automatically retry the SAVE operation on records when an error occurs because of resource unavailability. This functionality ensures that the records are eventually saved if the target data set is only temporarily unavailable, for example, because of load or network issues.
You can configure the default number of retries for the entire system in a dynamic system setting. To adjust the setting to different resource allocations and operating environments, you can update that number for each data flow run.
For more information, see Changing the number of retries for SAVE operations, Creating a batch run for data flows, and Creating a real-time run for data flows.
Additional case settings in App Studio
Valid from Pega Version 8.2
You can now make it easier to distinguish your case type from other case types by customizing its icon and selecting a unique case ID prefix in the General case settings.
You can also access Locking and Notifications case settings in App Studio without switching to Dev Studio.
For more information, see:
- Changing the case ID format
- Changing the case icon
- Managing concurrent access to a case
- Enabling case notifications
Update Existing Applications wizard will run for every upgrade
Valid from Pega Version 7.1.7
The upgrade process from a PRPC 5.x or 6.x system to Pega 7.1.7 now automatically runs the Update Existing Applications wizard. This may extend the time that the upgrade process takes to complete, depending on the version you are upgrading from and the number of rules in your application.
Improvements to OAuth 2.0 Services with Token Introspection Service and Token Denylist Service
Valid from Pega Version 8.5
Increase the security of user sessions by using the newly supported Token Introspection and Denylist services for OAuth 2.0.
Token Introspection service
Use the Token Introspection service to validate JSON Web Tokens (JWT). The Token Introspection service requires authentication.
Pega now uses OAuth 2.0 access tokens called Authorized Access Tokens (AAT).
Token Introspection service endpoint
The Token Introspection service endpoint provides the information about the status of access token and refresh token. Token introspection can be used to validate if a given token is still active or inactive. The token introspection endpoint determines whether the token is valid. The status indicates whether an access token or refresh token is valid or invalid:
- Valid tokens have the
“active”:truestatus - Invalid tokens have the
“active” :falsestatus.
The inactive status can also be due to revocation.
Token Denylist service
You can add tokens to the deny list in cases where suspicious activity might have occurred. The Token Denylist service provides a method for denying user access to the application by revoking the user's access token. This service can prevent a token from being used more than the specified number of times, which can be helpful in preventing replay attacks. Stolen tokens should be revoked using this service. A GET API is also available to get the list of denied tokens.
Keys endpoint
Pega Platform™ is changing from using opaque tokens to JSON Web (JWT) tokens. If this JWT is used by any other system, the public key is needed for signature verification. A new endpoint is exposed to provide these public keys in JWK format: https://host:port/prweb/api/oauth2/v1/token/keys.
For more information, see OAuth 2.0 Management Services.
Improved full text search
Valid from Pega Version 7.1.7
In Pega 7.1.7, Elasticsearch is used to provide full-text search functionality for rules, work, and data content, replacing the existing Lucene search functionality. In addition to providing search results two to five times more quickly than with Lucene Search, Elasticsearch is more scalable: with multi-threaded bulk and incremental indexing, it provides enhanced information about the search queue, the ability to host index files on multiple nodes, a more robust and expressive search parser, the ability to configure thresholds for alerts and search query time-outs, and automatic handling of replication and failover.
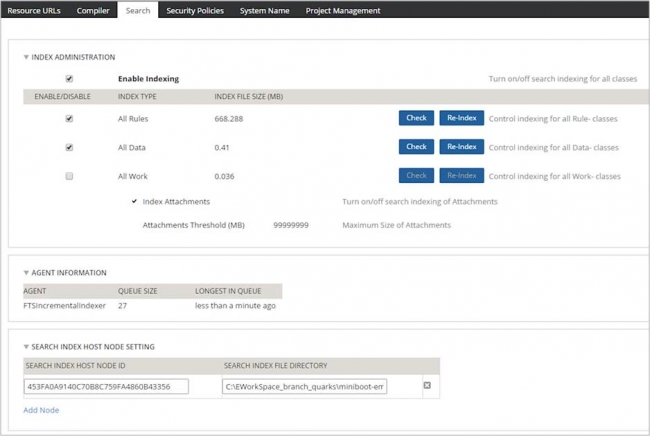
The search management user interface, where you can see length of queue and age of entries, which node hosts the search index, and where it is located.
After upgrading to Pega 7.1.7, the system administrator must manually migrate search functionality from Lucene Search to Elasticsearch. Note that during the switch-over and until the indexes are rebuilt, Lucene search continues to function and there is no interruption in search functions. For more information, see the Pega 7.1.7 Upgrade Guide.
Recommended heap sizes
Valid from Pega Version 7.1.7
The heap is a storage area in the Java virtual machine (JVM) allocated for both short-term and long-term (shared) object storage. If the server does not have enough memory allocated to run Pega 7, the system can hang without an error message. If this occurs, your values need to be higher than the recommendations based on your server hardware and the number of other applications on the server.
Pegasystems recommends using these settings:
- Initial Heap Size (Xms): 1 GB
- Maximum Heap Size (Xmx): 12 GB (8 GB minimum)
If your application server is using the Oracle JVM, also add the PermSize and MaxPermSize settings:
- PermSize (-XX:PermSize): at least 256MB
- MaxPermSize (-XX:MaxPermSize): at least 512MB
Set the JVM memory options to increase the amount of system memory allocated to the application server running Pega 7 by selecting and then selecting a listed node.
See the Pega 7.1.7 Installation Guides for more information about how to make these setting changes.
Auto-complete functionality optimized for mobile applications
Valid from Pega Version 7.1.7
When typing within a field in a mobile application, once a specified minimum number of search characters is entered, auto-complete functionality (pxAutoComplete) populates the entire screen with a list of suggestions. Tap an item in the list to select it for the specified field, or continue typing to ignore the suggestions.
This feature is only available for mobile applications running in Pega 7.1.7. Any previously created applications can utilize this auto-complete functionality if they are upgraded to run in Pega 7.1.7.
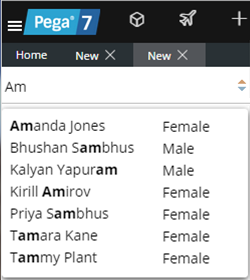
Start typing and auto-complete displays a list of suggested results
Define a taxonomy by using the Prediction Studio interface
Valid from Pega Version 8.1
Create a topic hierarchy and define keywords for each topic in Prediction Studio faster and more intuitively than by editing a CSV file. If you have already defined a taxonomy in a CSV file, you can import that file and modify existing topics and keywords by using the Prediction Studio interface.
For more information, see Creating-keyword-based topics for discovering keywords and Tutorial: Configuring a topic detection model for discovering keywords.
Improvements to automatic routing in the Email channel
Valid from Pega Version 8.1
To provide a broader range of use cases for a conversational channel developer, several new routing criteria have been added to the Email channel configuration. You can use detected language, a when rule, and keyword-based entities in the routing criteria when you set up the intelligent email routing capability for an Email channel.
For more information, see Intelligent routing and Configuring routing conditions for automatic email handling.

