Configuring SSO and LDAP
Deployment Manager supports LDAP and Single Sign-On (SSO) authentication, and assigns user roles based on the configuration settings in the active directory and SSO.
In Deployment Manager, the users or operators (other than
operators with the SuperAdmin role) must have an application associated with the user.
For SSO or LDAP integration, you must map the applications for the operator to the
accessibleApplications property. This property extends application accesses for each
operator without SuperAdmin privileges. When using accessibleApplications property to
specify multiple applications, the application must be comma separated (for example:
App1, App2).
- Create a new ruleset and create the property accessibleApplications. Set the class as Data-Admin-Operator-ID.
- Create a new application and only add the new ruleset created in Step 1 to the
application stack.
Adding an application ruleset to the application stack. 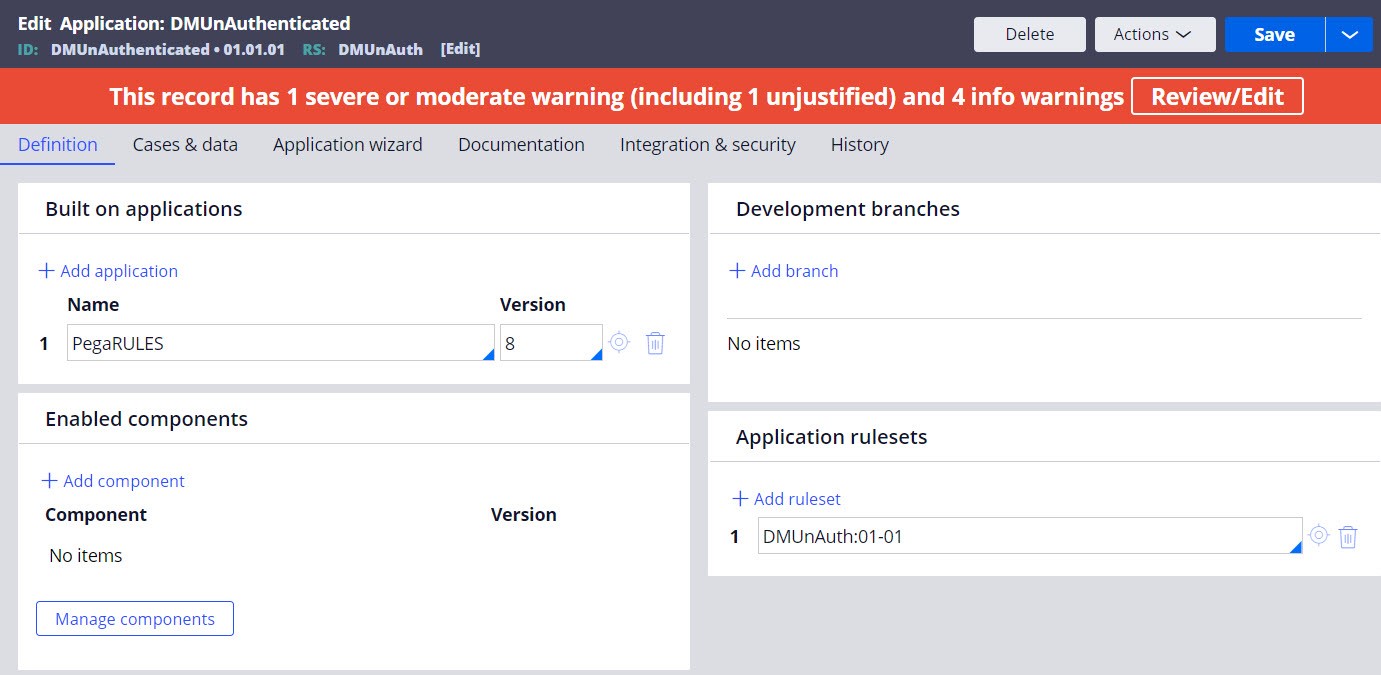
- Create a new Access Group and provide access to the new application that you
create in step 2. Provide this access group minimal access as this is assigned
to an unauthenticated user.
Limit the privileges for the access group. 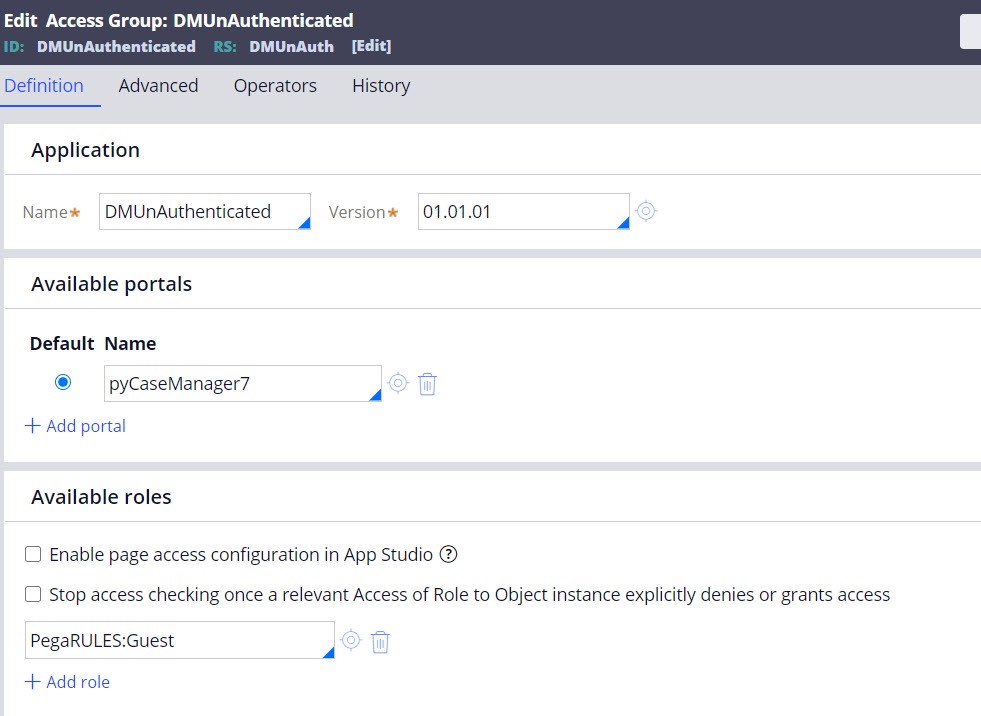
- Add the Access Group to the Access Group Name field in
the Browser Requestor Type screen.
Identify the system name and modify the access group for Browser Requestor Type. 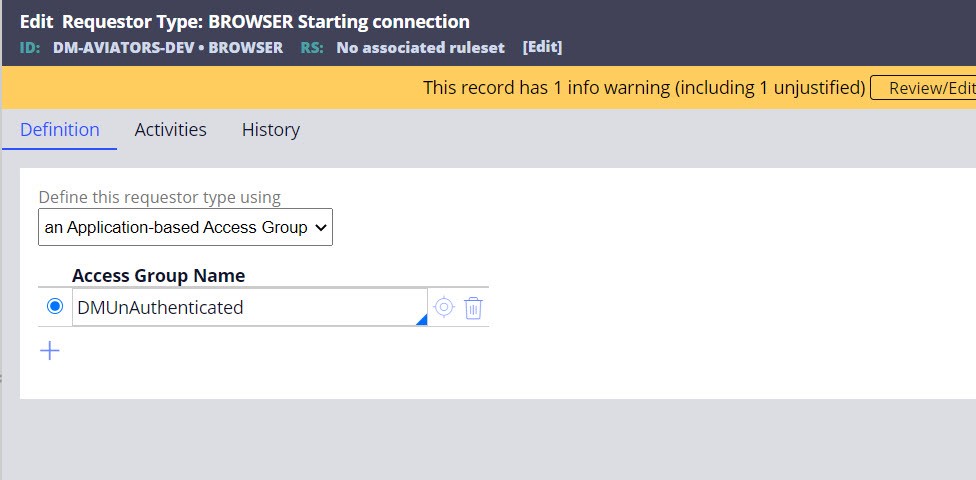
- Configure the LDAP or SSO authentication service to map attributes to the
accessibleApplications property, as shown in the
following figures:
LDAP mapping
Mapping LDAP attributes to the accessibleApplications property. 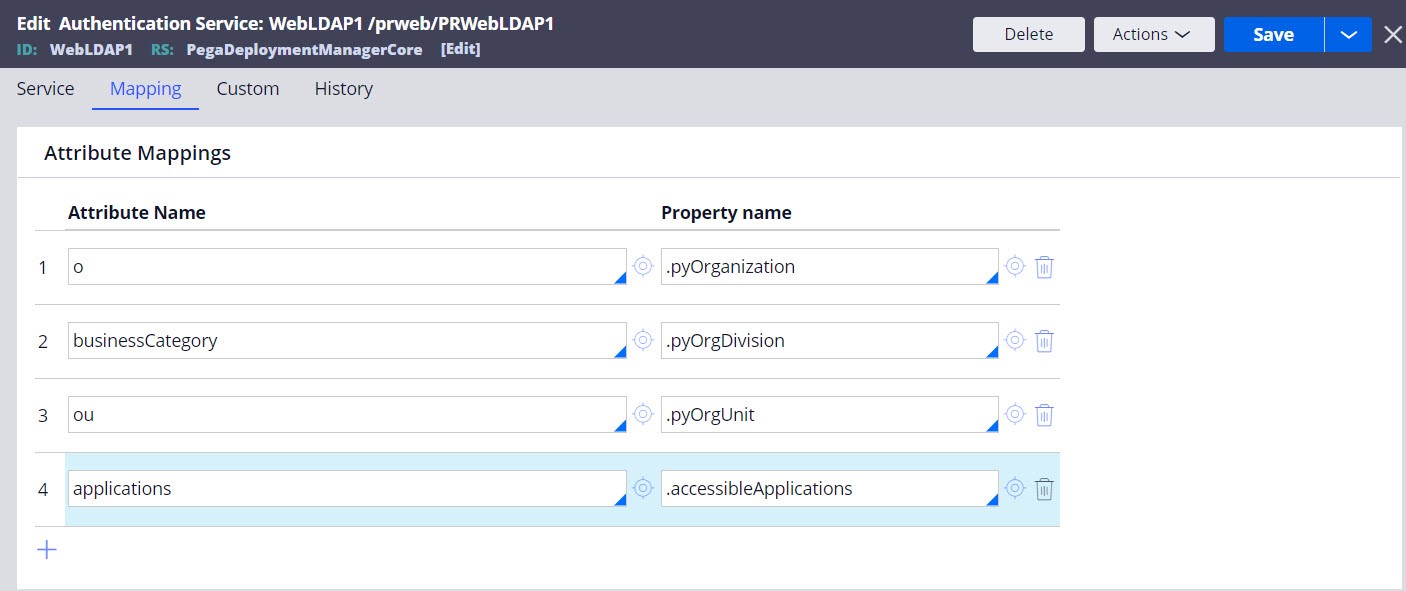
SSO mapping
Mapping LDAP attributes to the accessibleApplications property. 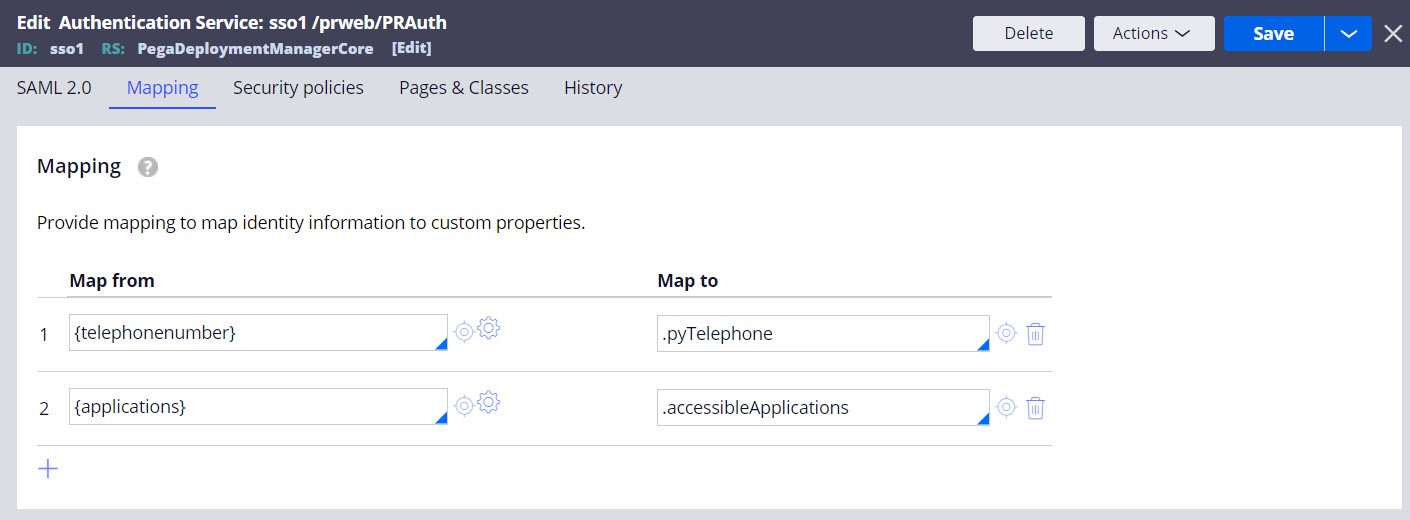
- To map applications externally, set dynamic system setting deploymentmanager/security/external_apps_mapping/enabled to True. If this is set to False, applications updated for operators in Deployment Manager will take precedence, and applications mentioned in the LDAP/SSO directory will not be applicable. For more information, see Dynamic system settings.
To assign the attribute to an operator, perform the following steps:
Previous topic Configuring pipelines to use test cases Next topic Creating and using custom tasks
