Using a script to replace a secure communication certificate
Pega Robotic Automation uses certificates to ensure secure communication between Pega Robot Runtime and the Pega applications that you have automated. Pega updates the certificate periodically, and includes the latest certificate in each Robot Runtime build. When you install or update Robot Runtime to the latest version, you receive the most current certificate (localruntime.pega.com). For more information, see Certificate expiration dates.
When you install Robot Studio or Robot Runtime using the Setup wizard or from the command line, a script runs to import the certificate and register the certificate on the port that you selected. When you use the Pega Synchronization Engine to update your environment, this script does not run. If you are using the Pega Synchronization Engine, you can follow these instructions to manually run the script, which will update the certificate and register the port.
To update the certificate without updating Robot Runtime, perform the following tasks in this order to replace the certificate:
- In a test environment, install the latest version of Robot Runtime.
- In a test environment, export the certificate.
- In a production environment, locate the port.
- In a production environment, run a batch or PowerShell script to install the certificate on your production computers.
Installing Robot Runtime to get the localruntime.pega.com certificate
- Download the latest version of Robot Runtime from Digital Delivery.
- In a test environment, follow the installation instructions to install Robot Runtime.
- In the Robotic Desktop Automation (RDA) Integration pane, select the Enable RDA Integration option. This option installs the certificate in the test environment.
Exporting the localruntime.pega.com certificate
During this task, you will need to note the following information, which you will use when you customize the script file:
- The hash value of the Thumbprint property.
- The password you choose to protect the Personal Information Exchange (PFX) file.
- The path to the certificate.
Follow these steps to use the Microsoft Management Console (MMC) to export the localruntime.pega.com certificate from the test environment.
- Click the Search icon on the task bar and enter mmc.exe. Right-click on mmc.exe and select Run as Administrator.
- Click
- In the Add or Remove Snap-ins window, under Available snap-ins, selectCertificates and click .
- Select the Computeraccountoption and click
- Choose Local computerandclick .
- In the Add or Remove Snap-ins window, click .
- Expand the Certificates (Local Computer) > Personalfolders under the Console root, and then select the Certificatesfolder.
- Double-click the localruntime.pega.com certificate and then click the Details tab.
- Scroll down to the Thumbprint property and note the hash value stored there. You will enter it in the script. Then click Copy to File.
- On the Certificate Export Wizard, click .
- Select the Yes, export the private key option and click .
- Select the Personal Information Exchange -PKCS #12 (.PFX) option, select the check boxes for the following options, and then click :
- Include all certificates in the certification path if possible
- Export all extended properties
- Enable certificate privacy
- Select the Password check box, then enter and confirm the password that you want to use to protect the PFX file. Note the password, and then click
- Enter a file name and location to export the certificate, and then click .
- Verify the file name and path and ensure that the Export Keys and Include all certificates in the certification path options are set to Yes, and the File Format is Personal Information Exchange (*.pfx). Note the path and then click .
Locating the port
In this task, you use a Robot Runtime computer in a production environment to locate and verify the port that Robot Runtime uses to communicate with the Pega application. Bind the localruntime.pega.com or your certificate's REST service to this port to ensure secure communications between Robot Runtime and the Pega application. The default port is 9443.
- In a text editor, open a RuntimeConfig.xml file used in a production environment. This file is located at %appdata%\pegasystem (for 19.1 and higher) or %appdata%\OpenSpan (for 8.0 SP1 and lower).
- In the Robotics > LocalApiService section, locate the port key. The value stored in this key is the port binding. Make a note of this value. The following is an example:
<LocalApiService enabled="true" SSL="true" port="9443" allowedOrigins="*pega.com" JWTSecurity="false" PegaServerURL="https://MyPegaServer.com/prweb"/>
Creating the script
You can create a batch or PowerShell script to make installing the certificate easier. Download and open the sample scripts from the following ZIP file:
Sample scripts for installing local Robot Runtime certificates
Customize these scripts to install the certificate. After you customize the script, run the saved script on each Robot Runtime computer that needs an updated certificate.
Customizing the batch file
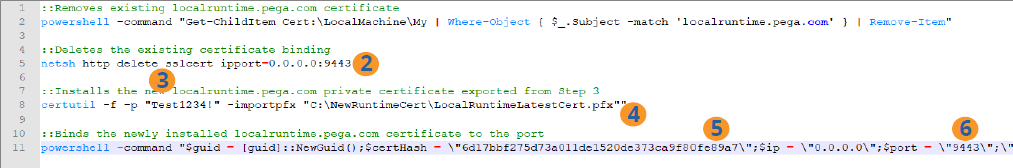
- Open the sample batch file in a text editor.
- Replace Line 5 - ipport PortNumber with the port number that you verified in the previous task.
- Replace Line 8 - p value with the password you used when exporting the certificate.
- Replace Line 8 - importpfx value with the path to the certificate.
- Replace Line 11 - $certHash value with the certificate hash value.
- Replace Line 11 - $port value with the port binding number.
- Save the batch file.
The following is an excerpt from the script in the sample batch file:
Customizing the PowerShell file
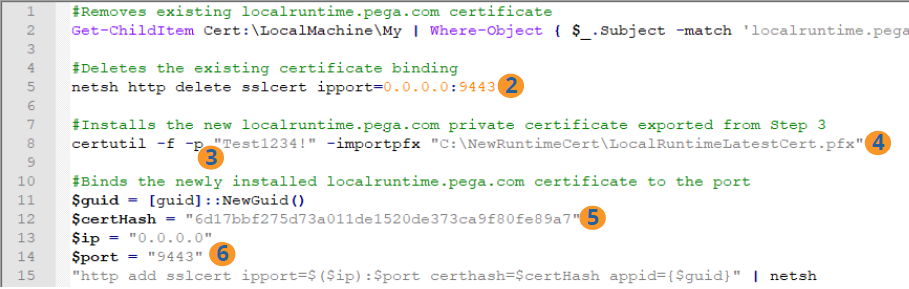
- Open the sample batch file in a text editor.
- Replace Line 5 - ipport PortNumber with the port number that you verified in the previous task.
- Replace Line 8 - p value with the password you used when exporting the certificate.
- Replace Line 8 - importpfx value with the path to the certificate.
- Replace Line 12 - $certHash value with the certificate hash value.
- Replace Line 14 - $port value with the port binding number.
- Save the PowerShell file.
The following is an excerpt from the script in the sample PowerShell file:
Previous topic Checking your certificate expiration date Next topic Replacing the Pega RDA certificate with a self-provisioned certificate
